
Database System Concepts
7th Edition
ISBN: 9780078022159
Author: Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher: McGraw-Hill Education
expand_more
expand_more
format_list_bulleted
Question
i need the answer quickly
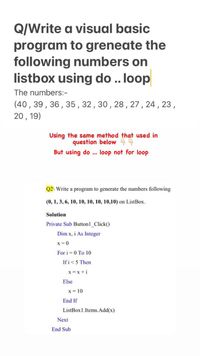
Transcribed Image Text:Q/Write a visual basic
program to greneate the
following numbers on
listbox using do .. loop
The numbers:-
(40, 39, 36, 35 , 32,30,28,27 , 24 , 23 ,
20, 19)
Using the same method that used in
question below
But using do . loop not for loop
Q2\ Write a program to generate the numbers following
(0, 1, 3, 6, 10, 10, 10, 10, 10,10) on ListBox.
Solution
Private Sub Button1 Click()
Dim x, i As Integer
x=0
For i = 0 To 10
Ifi<5 Then
x =x +i
Else
x = 10
End If
ListBox1.Items.Add(x)
Next
End Sub
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 4 steps with 1 images

Knowledge Booster
Learn more about
Need a deep-dive on the concept behind this application? Look no further. Learn more about this topic, computer-science and related others by exploring similar questions and additional content below.Similar questions
- Please explain the answer and show the final answerr !! f18arrow_forwardIs our society becoming more or less united as a result of technical developments like the internet?arrow_forwardDetail how you solved the password. what method can you use A written report : including screen captures, diagrams, tables, and charts. for example: Suppose Alice sent the following secret message: 001000000100100100111001001010000011101000111010 The decryption key was discovered to be:01101001arrow_forward
- Alice sends a message to Bob, along with a digital signature created by encrypting a hash of the message. Which key did Alice use to encrypt the hash? Why is that the appropriate key? Which key will Bob use to verify the digital signature? Why is that the appropriate key?arrow_forwardDecode the number using the given private key. Decode the number M = 15 using the private key d = 53 and n= 77. Assume you are decoding the number using the RSA cryptosystem. Note: You can use the Modular Exponentiation calculator to help with the calculation.arrow_forwardIn the RSA system described in the notes, take p = 101, q = 103, and k = 1249. Determine the public key (a,n). a= n=arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education

Database System Concepts
Computer Science
ISBN:9780078022159
Author:Abraham Silberschatz Professor, Henry F. Korth, S. Sudarshan
Publisher:McGraw-Hill Education

Starting Out with Python (4th Edition)
Computer Science
ISBN:9780134444321
Author:Tony Gaddis
Publisher:PEARSON

Digital Fundamentals (11th Edition)
Computer Science
ISBN:9780132737968
Author:Thomas L. Floyd
Publisher:PEARSON

C How to Program (8th Edition)
Computer Science
ISBN:9780133976892
Author:Paul J. Deitel, Harvey Deitel
Publisher:PEARSON

Database Systems: Design, Implementation, & Manag...
Computer Science
ISBN:9781337627900
Author:Carlos Coronel, Steven Morris
Publisher:Cengage Learning

Programmable Logic Controllers
Computer Science
ISBN:9780073373843
Author:Frank D. Petruzella
Publisher:McGraw-Hill Education