
Write a Java TCP MultipleClient-Server
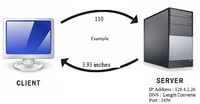
NOTE Server Details are in the above figure
- Client-Server communicates continuously until the Client send Bye to the Server
- Use Multithreading for Multiple Clients
NOTE :
1 cm = 0.39 inches
1 cm = 0.03 foot
1 cm = 0.01 meter
Sample Ouput:
|
Client |
Server |
|
1 – cm to inches 2 – cm to foot 3 – cm to meter Enter length in cms (int) : 10 Received from Server 3.9 inches
1 – cm to inches 2 – cm to foot 3 – cm to meter Enter length in cms (int) : BYE Received from Server BYE
Client DISCONNECTED |
Server Waiting for the Cline to be Connected… CONECTION ESTABLISHED
Received From Client 10 cms Sent to Client 3.9 inches
Received From Client BYE Sent to Client BYE |
HINT : When client choses 1 for cm to inches and enter 10, then the client sends the string 110 to the Server. Where the first char ‘1’ represents the cm to inches and the other 2 chars represents the 10.

Step by stepSolved in 2 steps

- TCP MULTIPLEXING AND DEMULTIPLEXING In the scenario below, the left and right TCP clients communicate with a TCP server using TCP sockets. The Python code used to create a single welcoming socket in the server is shown in the figure (the welcoming socket itself is not shown graphically); code is also shown for the client sockets as well. The three sockets shown in server were created as a result of the server accepting connection requests on this welcoming socket from the two clients (one connection from the client on the left, and two connections from the client on the right). mySocket = socket (AF_INET, SOCK_STREAM) mySocket.bind (myaddr, 6189 ); P1 Answer mySocket = socket (AF_INET, SOCK_STREAM) mySocket.bind (myaddr, 5854 ); ♫ transport QUESTION 1 OF 8 network link physical What is the source port # for packet C? www B source port: ? dest port: ? P4 HIGH A source port: ? dest port: ? P5 P6 transport network lirk physical mySocket1 = socket (AF_INET, SOCK_STREAM) mySocket1.bind…arrow_forwardUSING JAVA (Java Socket /TCP Programming) Create a chat/messaging application that has the following functionalities/features: Broadcast message (to all users) Private message to only one message (established usernames are stored in an XML file)arrow_forwardHow do handler interfaces accommodate the integration of newer protocols or communication standards?arrow_forward
- Is it feasible for an application to make use of UDP while maintaining a dependable data delivery mechanism? If such is the case, what steps would you take to accomplish your goal?arrow_forwardWhile developing a reliable transport protocol, early versions of the protocol discussed in class used a NAK message, sent by the receiver to the sender to indicate a packet was not correctly received. This kind of message, however, is not found in further protocols, like GBN, SR or even TCP. Why not? In other words, why don't these protocols provide a way to signal to the sender that the received message was received with an errorarrow_forwardConnectionless protocols have been suggested as a solution for connection-based protocols. Describe the pros and cons of these protocols.arrow_forward
- C PROGRAMMING you are to write a TCP/IP server that can build up a graph of a network ofnetworks (using the supplied graph library and implementation of Dijkstra’s algorithm) and thenquery that graph to find out which link between two networks should be used as the next hop tosend a packet of data from one network to another within the network of networks (using thesupplied implementation of Dijkstra’s algorithm). using the following program as a start point: /* * NetworkServer.c * ProgrammingPortfolio Skeleton * */ /* You will need to include these header files to be able to implement the TCP/IP functions */#include <stdio.h>#include <stdlib.h>#include <string.h>#include <sys/types.h>#include <netinet/in.h>#include <netdb.h>#include <fcntl.h>#include <unistd.h>#include <errno.h>#include <sys/socket.h> /* You will also need to add #include for your graph library header files */ int main(int argc, const char * argv[]){ int…arrow_forwardWhat are the two strongest justifications for layered protocols?arrow_forwardPlease define random access method and identify the two protocols that fall under this umbrella.arrow_forward
 Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education
Database System ConceptsComputer ScienceISBN:9780078022159Author:Abraham Silberschatz Professor, Henry F. Korth, S. SudarshanPublisher:McGraw-Hill Education Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON
Starting Out with Python (4th Edition)Computer ScienceISBN:9780134444321Author:Tony GaddisPublisher:PEARSON Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON
Digital Fundamentals (11th Edition)Computer ScienceISBN:9780132737968Author:Thomas L. FloydPublisher:PEARSON C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON
C How to Program (8th Edition)Computer ScienceISBN:9780133976892Author:Paul J. Deitel, Harvey DeitelPublisher:PEARSON Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning
Database Systems: Design, Implementation, & Manag...Computer ScienceISBN:9781337627900Author:Carlos Coronel, Steven MorrisPublisher:Cengage Learning Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education
Programmable Logic ControllersComputer ScienceISBN:9780073373843Author:Frank D. PetruzellaPublisher:McGraw-Hill Education





