
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
Please use the alphabet shown in the screenshot below to code a Depth-first search (DFS)

Transcribed Image Text:Depth-first search Algorithm
• Push the root node on a stack;
while (stack is not empty) {
remove (pop) the top node from the stack;
if (node is a goal node) return success;
Push all children of node onto the stack;
}
return failure;
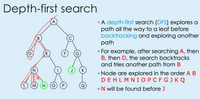
Transcribed Image Text:Depth-first search
• A depth-first search (DFS) explores a
path all the way to a leaf before
backtracking and exploring another
path
В
C
For example, after searching A, then
B, then D, the search backtracks
and tries another path from B
D
F
G
J
K
Node are explored in the order A B
DEHLMNIOPCFGJKQ
Q
•N will be found before J
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- please use c# i just want you to modify the code please Download the solution and run it locally. Familiarize yourself with the code, then modify it as follows: 1. Replace the use of depth first search with the breadth first search algorithm. 2. Add at least 5 more employees // The code below was mostly taken directly from:// https://www.csharpstar.com/csharp-depth-first-seach-using-list/using System;using System.Collections.Generic;using System.Linq;using System.Text;using System.Threading.Tasks; namespace depthFirstSearch{ class Program { public class Employee { public Employee(string name) { this.name = name; } public string name { get; set; } public List<Employee> Employees { get { return EmployeesList; } } public void isEmployeeOf(Employee e) {…arrow_forwardC++languagearrow_forwardC++arrow_forward
- Sum of two squares def sum_of_two_squares(n): Some positive integers can be expressed as a sum of two squares of some positive integers greater than zero. For example, 74 = 49 + 25 = 7^2 + 5^2. This function should find and return a tuple of two positive integers whose squares together add up to n, or return None if the parameter n cannot be broken into a sum of two squares.To facilitate the automated testing, the returned tuple must present the larger of its two numbers first. Furthermore, if some integer can be broken down to a sum of squares in several ways, return the breakdown that maximizes the larger number. For example, the number 85 allows two such representations 7^2 + 6^2 and 9^2 + 2^2 , of which this function must return (9, 2).The technique of two approaching indices that start from the beginning and end of a sequence, respectively, and approach each other until they meet somewhere is directly applicable to this problem. In this problem, these indices crawl towards each…arrow_forward>> IN C PROGRAMMING LANGUAGE ONLY << COPY OF DEFAULT CODE, ADD SOLUTION INTO CODE IN C #include <stdio.h>#include <stdlib.h>#include <string.h> #include "GVDie.h" int RollSpecificNumber(GVDie die, int num, int goal) {/* Type your code here. */} int main() {GVDie die = InitGVDie(); // Create a GVDie variabledie = SetSeed(15, die); // Set the GVDie variable with seed value 15int num;int goal;int rolls; scanf("%d", &num);scanf("%d", &goal);rolls = RollSpecificNumber(die, num, goal); // Should return the number of rolls to reach total.printf("It took %d rolls to get a \"%d\" %d times.\n", rolls, num, goal); return 0;}arrow_forwardHow difficult is it to duplicate a collection of shared pointers into another array while using the C++ programming language? Create a list of the several approaches you may use to tackle the issue that has been presented to you. Is it the case that copying a shared pointer also copies the objects that it controls? Explainarrow_forward
- Caesars Cypher in C programming language How do you program an encryption and decryption for a Caesars Cypher that covers all the possible ASCII characters? In this there should be a shift over K = 5 but the example below is K = 3. This should result in actual character and not the control ASCII represenations. For example: >>> $ encrypt(I have a key)N%mf{j%f%pj~>>> $ encrypt(see me at 3)xjj%rj%fy%8>>> $ decrpyt(|jfw%ns%gqzj)wear in blue Assume that the text parsing method has been succesful and it's the encryption/decryption of the char array that needs to be factored. Formula Encryption -> C = E(k, P) = (P + k) (mod 26) Decryption -> P = D(k, C) = (C - k) (mod 26) Where k = 5arrow_forwardIn C++ Assume that a 5 element array of type string named boroughs has been declared and initialized. Write the code necessary to switch (exchange) the values of the first and last elements of the array.arrow_forwardPlease provide a C++ function template that can be used to sort an array of various data types.arrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY