
Computer Networking: A Top-Down Approach (7th Edition)
7th Edition
ISBN: 9780133594140
Author: James Kurose, Keith Ross
Publisher: PEARSON
expand_more
expand_more
format_list_bulleted
Question
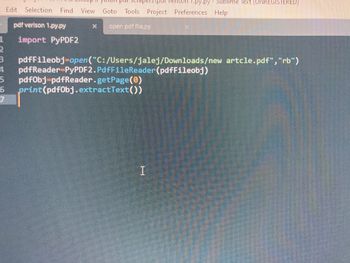
I need help with a school project! My task is to extract a pdf file using python and output it in my sublime text IDE. What I need is to extract a pdf file and get all page numbers. In my example code I’m about to extract the first page number but need all pages numbers to be extracted! What can I do to fix this?
Transcribed Image Text:Edit Selection Find View Goto Tools Project Preferences Help
open pdf file.py
verison 1.py.py - Sublime Text (UNREGISTERED)
pdf verison 1.py.py
1 import PyPDF2
2
3 pdfFileobj=open("C:/Users/jalej/Downloads/new artcle.pdf", "rb")
4 pdfReader=PyPDF2.PdfFileReader(pdfFileobj)
5
6
7
pdfObj=pdfReader.getPage (0)
print (pdf0bj.extractText())
I
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
Step by stepSolved in 2 steps

Knowledge Booster
Similar questions
- Imagine you have a spreadsheet with exactly one row of data—row 2—that has three cells with data in it. You want to copy that row to row 1. Describe how you would cut and paste row 2 to row 1 using only key commands (no mouse clicks or menu selections). For the arrows, up, down, left, and right are sufficient; for hotkey commands that require two keys pressed at once, use a + symbol between the keys (e.g., Shift + Z for undo). You start in cell A1.arrow_forwardWrite a program to handle a user's rolodex entries. (A rolodex is a system with tagged cards each representing a contact. It would contain a name, address, and phone number. In this day and age, it would probably have an email address as well.) Typical operations people want to do to a rolodex entry are: 1) Add entry 2) Edit entry 3) Delete entry 4) Find entry 5) Print all entries 6) Quit You can decide what the maximum number of rolodex entries is and how long each part of an entry is (name, address, etc.). When they choose to edit an entry, give them the option of selecting from the current rolodex entries or returning to the main menu — don't force them to edit someone just because they chose that option. Similarly for deleting an entry. Also don't forget that when deleting an entry, you must move all following entries down to fill in the gap. If they want to add an entry and the rolodex is full, offer them the choice to return to the main menu or select a person to overwrite. When…arrow_forwardWrite Python commands, within a print command, that output the following. (E.g. print(list(range(10))) , in spyder (vi) Let x = [1,3,5] and let y = [2,4,6]. If we interpret these as vectors x and y then the vector sum can be written x + y = [x[0]+y[0],x[1]+y[1],x[2]+y[2]]. Find an the equivalent expression for the vector dot product x⋅y. (vii) With x,y as above find an expression for the vector cross product x * y.arrow_forward
- use https://live.sympy.org/ (Links to an external site.) Review the examples about cardinality in Python using Sympy- https://www.geeksforgeeks.org/sympy-subset-cardinality-in-python/ (Links to an external site.) Explain each one, and what the result means Provide a link or a screenshot of working codearrow_forwardUSING KEIL PLEASE.. Ciphers use many bitwise operations for cryptography. Write an ARM assembly program to use ciphers. See the steps below to implement the cipher. In this program, you will implement a "Symmetric Encryption". Create three variables, Plaintext, Key, and Cipher (5 Points) For encryption, design a key value, assign the last nonzero number of your student ID (#900 number) in a variable called “Key” (5 Points) For example: if your 900 number is 90012450. Assign 5 to the variable Key and use it as the Key for encryption. Use this link for the Links to an external site.video to understand Symmetric Key Cryptography and implement that for encryption and decryption. For the variable Plaintext, assign any four-letter word. Encrypt the plaintext using the value in Key and store the encrypted text in the variable Cipher. Test the encryption by decrypting and storing the decrypted text into register R5. Provide comments to each statementarrow_forward
arrow_back_ios
arrow_forward_ios
Recommended textbooks for you
 Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON
Computer Networking: A Top-Down Approach (7th Edi...Computer EngineeringISBN:9780133594140Author:James Kurose, Keith RossPublisher:PEARSON Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science
Computer Organization and Design MIPS Edition, Fi...Computer EngineeringISBN:9780124077263Author:David A. Patterson, John L. HennessyPublisher:Elsevier Science Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning
Network+ Guide to Networks (MindTap Course List)Computer EngineeringISBN:9781337569330Author:Jill West, Tamara Dean, Jean AndrewsPublisher:Cengage Learning Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning
Concepts of Database ManagementComputer EngineeringISBN:9781337093422Author:Joy L. Starks, Philip J. Pratt, Mary Z. LastPublisher:Cengage Learning Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education
Prelude to ProgrammingComputer EngineeringISBN:9780133750423Author:VENIT, StewartPublisher:Pearson Education Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY
Sc Business Data Communications and Networking, T...Computer EngineeringISBN:9781119368830Author:FITZGERALDPublisher:WILEY

Computer Networking: A Top-Down Approach (7th Edi...
Computer Engineering
ISBN:9780133594140
Author:James Kurose, Keith Ross
Publisher:PEARSON

Computer Organization and Design MIPS Edition, Fi...
Computer Engineering
ISBN:9780124077263
Author:David A. Patterson, John L. Hennessy
Publisher:Elsevier Science

Network+ Guide to Networks (MindTap Course List)
Computer Engineering
ISBN:9781337569330
Author:Jill West, Tamara Dean, Jean Andrews
Publisher:Cengage Learning

Concepts of Database Management
Computer Engineering
ISBN:9781337093422
Author:Joy L. Starks, Philip J. Pratt, Mary Z. Last
Publisher:Cengage Learning

Prelude to Programming
Computer Engineering
ISBN:9780133750423
Author:VENIT, Stewart
Publisher:Pearson Education

Sc Business Data Communications and Networking, T...
Computer Engineering
ISBN:9781119368830
Author:FITZGERALD
Publisher:WILEY