Question
Transcribed Image Text:9:05
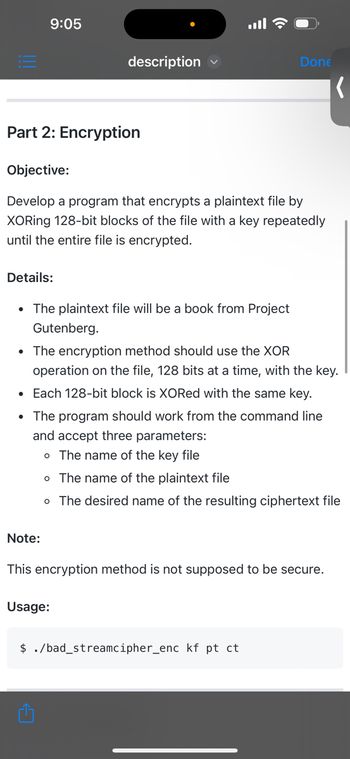
Part 2: Encryption
Details:
description
Objective:
Develop a program that encrypts a plaintext file by
XORing 128-bit blocks of the file with a key repeatedly
until the entire file is encrypted.
• The plaintext file will be a book from Project
Gutenberg.
Note:
Done
• The encryption method should use the XOR
operation on the file, 128 bits at a time, with the key.
• Each 128-bit block is XORed with the same key.
• The program should work from the command line
and accept three parameters:
o The name of the key file
Usage:
o The name of the plaintext file
o The desired name of the resulting ciphertext file
This encryption method is not supposed to be secure.
(
$ ./bad_streamcipher_enc kf pt ct
Transcribed Image Text:9:05
description
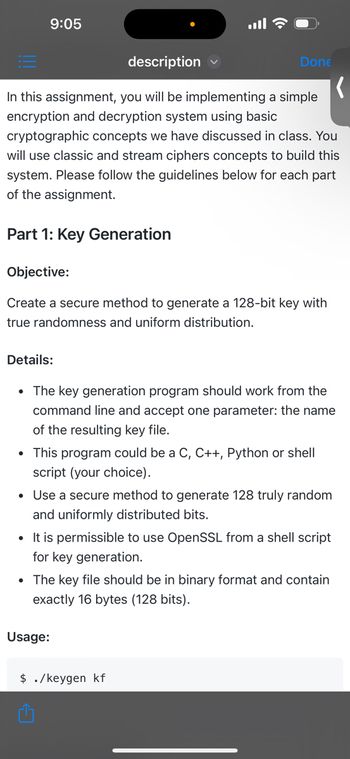
In this assignment, you will be implementing a simple
encryption and decryption system using basic
cryptographic concepts we have discussed in class. You
will use classic and stream ciphers concepts to build this
system. Please follow the guidelines below for each part
of the assignment.
Part 1: Key Generation
Objective:
Create a secure method to generate a 128-bit key with
true randomness and uniform distribution.
Done
Details:
• The key generation program should work from the
command line and accept one parameter: the name
of the resulting key file.
• This program could be a C, C++, Python or shell
script (your choice).
• Use a secure method to generate 128 truly random
and uniformly distributed bits.
• It is permissible to use OpenSSL from a shell script
for key generation.
• The key file should be in binary format and contain
exactly 16 bytes (128 bits).
Usage:
$ ./keygen kf
(
Expert Solution
This question has been solved!
Explore an expertly crafted, step-by-step solution for a thorough understanding of key concepts.
This is a popular solution
Trending nowThis is a popular solution!
Step by stepSolved in 4 steps with 4 images

Knowledge Booster
Similar questions
- Why is hashing passwords preferable than encryption when storing passwords in a file?arrow_forwardWhy is hashing better than encryption for file-stored passwords?Why and how do password files work?arrow_forwardWhy is hashing better than encryption when a password must be stored in a file? The function of a password file, and how to use it, are both explained.arrow_forward
- 1. An open hashing scheme requires the use of random access ( true /false ). 2. A good hashing function should ___ distribute the records amongthe buckets. 3. For an open hashing scheme with 100 buckets and 4000 records,the average number of record reads to locate a record is equal to___.arrow_forwardQuestion # 1: Use the Multiplicative Cipher method to encrypt the following plaintext:We will succeed in our ventureKey length K = 7 You must show all the steps of your workQuestion # 2: Use the additive cipher with key = 15 to decrypt the message “WTAAD”.You must show all the steps of your work Question # 3: Use the concept of a one-way hash function to encrypt the following name into a 9 x 9 -dimensional database table. Jonathan Leea) How many rows and columns are there on this tableb) Which indices is Jonathan on this tablec) Why are hash functions relevant in database encryption?d) What would you do to remedy the problem of index congestion on your database?You must show all the steps of your work Question # 4: Use the multiplicative method to decrypt the following ciphertext.MADWU Key = 5You must show all the steps of your workQuestion # 5: use the XOR technique to encrypt the following statement before transmission: The quick brown fox jumps over the lazy dogarrow_forwardWhen it comes to PKI (Public Key Infrastructure) In order to get B's public key, A must first submit a request to the Public Key Authority, which will then generate and send a message to B (E(PRauth[PUB] || Request || Time1]). It's debatable which key A should use to interpret the message.arrow_forward
- Digital forensics: Suppose that we a record but not sure which one is the original one and which one has been modified: A) Bob leaves the hotel at 7:00 pm B) Bob leaves the hotel at 6:00 pm Fortunately, we have the hash value of the original record, calculated by SHA-256: 2655a8151189efae706db96460d368ab6adb9f5a1b88e5aa5c6ea18ba65beadd Please tell us which one is the original one, A or B? (Hint: You can use the SHA-256 calculator at https://xorbin.com/tools/sha256-hash-calculator).arrow_forwardWhy is hashing passwords saved in a file preferable to encryption?arrow_forwardWhy does hashing a file that includes user passwords make more sense than encrypting the passwords in that file?arrow_forward
- Given the following input (4322, 1334, 1471, 9679, 1989, 6171, 6173 and 4199) and the hash function x mod 10, which of the following statements are true? i. 9679, 1989, 4199 hash to the same value ii. 1471, 6171 hash to the same value iii. All elements hash to the same value iv. Each element hashes to a different value I only i and ii ii only ili and ivarrow_forwardUsing 31452 as encryption key for transposition cipher, encrypt the following replacing "your name" by your first and last name: "your name" will be attending all classes this semester Next verify your encryption by first making a decryption key and then decrypting your ciphertext by illustrating the decryption process.arrow_forwardWhy is hashing superior to encryption when storing a passphrase in a file? The function and usage of a password file are both explained.arrow_forward
arrow_back_ios
SEE MORE QUESTIONS
arrow_forward_ios